
How can IJ-Net provide you with the right type of VPN and security access
What is a VPN?
Pronounced as separate letters, it's short forVirtual Private Network, a network that is constructed by using public
wires to connect nodes. For example, there are a number of systems that enable you to create networks using the Internet
as the medium for transporting data. These systems use encryption and other security mechanisms to ensure that only
authorized users can access the network and that the data cannot be intercepted.
A VPN connection is a point-to-point connection between the userís computer and the companyís server that allows
private data by mobile employees, telecommuters, business partners and remote sites to be sent securely over a shared
or public network, such as the Internet. With Virtual Private Networks, communication links between users and sites can
be achieved quickly, inexpensively and safely across the world.(Figure 1)
Figure 1: VPN Connection
Laptop user can connect to company network.
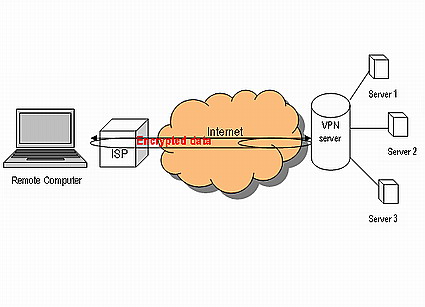
VPN connections can be established from almost anywhere around the world and that is why networks need strong
security features to prevent unwelcome access to private networks and to protect private data as it traverses
the public network. However, as data travels between users and their remote offices, it can pass through 25 or
more different servers around the world before reaching its final destination. Because there are many opportunities
for hackers here, the data should be secured through some form of encryption. That is why VPNs provide data
privacy with encryption techniques where encryption scrambles clear text (message) into cipher text. The cipher text
is then sent to the recipient, who decrypts the message back into clear text again.
All Rights Reserved © 2004