
What can IJ-Net do to protect you or your company from unwanted intrusion?
IJ-Net can provide a cost effective firewall solution that will prevent external attack. Firewalls come in
two forms,
hardware based or software based. Hardware firewalls are currently the best defense system for
small or large
companies, and these devices tend to be placed between the internet and your network or computers.
Software based firewalls can be installed and running on either the users computer or laptop, or on a dedicated
computer that sits in between the internet and your network, in both situations IJ-Net do not recommend the use
of software based firewall as
see Figure 2.
What is a Firewall?
A computer firewall protects networked computers from intentional hostile intrusion that could compromise
confidentiality
or result in data corruption or denial of service. It may be a hardware device (Figure 1)
or a software program
(Figure 2) running on a secure host computer. In either case, it must have at least
two network interfaces, one for the
network it is intended to protect, and one for the network it is exposed
to. A network firewall sits at the junction point or
gateway between the two networks, usually a private
network and a public network such as the Internet.
The earliest computer firewalls were simple routers. The term "firewall" comes from the fact that by segmenting
a network
into different physical subnetworks, they limited the damage that could spread from one subnet to another
- just like firedoors or firewalls.
Figure 1: Hardware Firewall
Hardware firewall providing protection to a Local Network
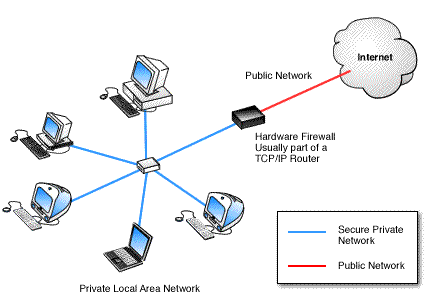
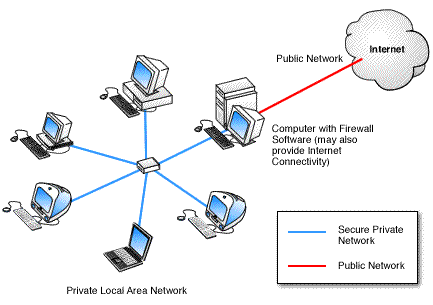
Figure 2: Computer with Firewall Software
Computer running firewall software to provide protection
What does a firewall do?
An Internet firewall examines all traffic routed between your network and the Internet to see if it meets certain criteria.
If it does, it is routed between the networks, otherwise it is stopped. A network firewall filters both inbound and outbound
traffic. It can also manage public access to private networked resources such as host applications. It can be used to log
all attempts to enter the private network and trigger alarms when hostile or unauthorized entry is attempted. Firewalls can
filter packets based on their source, destination addresses and port numbers. This is known as address filtering. Firewalls
can also filter specific types of network traffic. This is also known as protocol filtering because the decision to forward
or reject traffic is dependant upon the protocol used, for example HTTP, ftp or telnet. Firewalls can also filter traffic
by packet attribute or state.
All Rights Reserved © 2004